Mobile Money systems are known to be secure from the first node to the customer interaction interface. Well, last week, this was proved wrong by a group of unknown black hat hackers who discovered a 3rd party vulnerability and utilized it to their advantage.
In IT security, hacker backdoors are often realized through the interoperability of various systems running different code. In the case of MTN Mobile Money and Airtel Money, the ability for customers to make direct bank and cross-network transfers caused a vulnerability.
Reportedly, Pegasus Technologies – a Ugandan IT systems company is one of the authorized MTN Mobile Money and Airtel Money API providers that make it possible for customers to transact with specific underlying services including the ability to transact with bank accounts.
Other known authorized Mobile Money API companies in Uganda include Africa is Talking, Beyonic, Yo Uganda, among many others. But in the course of last week, Pegasus Technologies reportedly fell prey of attackers that robbed MTN and Airtel Money funds with Stanbic Bank as their stable link of choice.
How Hackers attacked MTN Mobile Money and Airtel Money
With Cybersecurity as a growing concern in the world, backdoors are known to be present in several IT systems including most sophisticated services hosted in secure and well set up data centers.
Through a vulnerable backdoor reportedly discovered at Pegasus Technologies, Hackers got direct access to Mobile Money systems by disguising transactions as valid processes between customers and Stanbic Bank as well as to other telcos (MTN – Airtel and Vice versa).
Notably, Pegasus handles MTN-Airtel and Airtel-MTN as well as other telco to telco mobile money transfer processes. On top of that, the company handles Stanbic Bank’s Flexi Pay service that allows customers to pay for goods and services using mobile money.
So, on Thursday 1st October 2020, Hackers plotted a rogue attack on Pegasus systems and disguised silent transactions as MTN to Airtel, Airtel to MTN, MTN to Stanbic Bank, and Airtel to Stanbic Bank, as well as Stanbic Bank to Mobile money transfers.
Routing safely through Thursday night, to Friday, until Saturday. Within the short timeframe, hackers had reportedly sent themselves over UGX 1.3 Billion, withdrawn over UGX 900 Million on Airtel money, and double the amount through MTN Mobile Money.
“From Thursday night, the hack went on undetected until Saturday. By this time, hackers had sent themselves almost UGX1.3 billion but had managed to withdraw UGX900 million from Airtel Money. We estimate MTN also lost almost twice the same amount of money since they are mobile money leaders. When the fraud was detected all transactions going through Pegasus Technologies, were suspended,”
A Source told the CEO East Africa Magazine
With only IGX 1.3billion earmarked as an estimate, the hackers may have transacted more money to each other within the dark timeframe (Thursday night to Saturday) before being blocked out. So, the figure is estimated to be higher with more billions of shillings expected to be declared as lost.
Why Hackers Targeted MTN, Airtel and Stanbic
- Financial Gain (Theft)
- Utilize the chance of a vulnerable backdoor (failed/corrupt databases)
- Steal customer funds (mobile money and bank balances)
- To bankrupt mobile money service operators and cause insecurity beliefs/alarms.
Apparently, several Ugandan news blogs have attached the recent hacks to the growing political atmosphere in Uganda. However, by pure standards, the hack is not associated with any political movement or pressure resulting into the loss of funds by the trio.
Instead, a group of hackers utilised a backdoor (Pegasus) to gain control over mobile money transactions, and in the end transferred a huge sum of money between owned accounts with only UGX 1.3billion sighted as the leaked amount at the moment.
Hence, the core reason why hackers attacked mobile money systems hosted by MTN, Airtel and further used Stanbic bank as an extra gateway through a 3rd party portal, was to utilise the End of Month window (a peak timeframe for Bank and mobile money transactions) to run rogue code, and sniff targeted brands.
By IT security standards, the vulnerability option may have been located in Pegasus’ systems code. Although IT companies route with closed source code/software not supported with GNU licenses (open source), a vulnerability in code can’t fail to miss in the mix which could be with a missing update or system fault.
While speaking to CEO Magazine, the Pegasus Technologies Managing Director Ronald Azirwe could neither admit that hackers attacked through a backdoor at the company nor deny as he said:
“Sadly I can’t comment on that. I can’t confirm or deny anything of the sort. I can’t speak about it. MTN/Stanbic/Airtel should be able to tell you whether it is Pegasus or not,”
Mr. Ronald Azirwe told a reporter
The MTN, Airtel, and Stanbic Security Response to the Attacks
Through a Joint press release shared with the Tech Point Magazine team, MTN, Airtel, and Stanbic acknowledged the presence of an issue that hit the institutions, but didn’t spread to customer accounts noting that account balances were not affected.
Stanbic Bank Uganda, MTN Uganda and Airtel Uganda inform the public and their customers that on Saturday 3 October 2020, a third-party service provider experienced a system incident which impacted Bank to Mobile Money transactions. All Bank to Mobile Money/Wallet services have since been temporarily suspended.
This system incident has had no impact on any balances on both Bank and Mobile Money accounts.
Our technical teams are analysing the incident and will restore services as soon as possible.
We apologise to all customers for any inconvenience that this has caused and reiterate our commitment to delivering seamless banking and mobile money services.
Regards,
| Anne Juuko Chief Executive Stanbic Bank Uganda | Wim Vanhelleputte Chief Executive Officer MTN Uganda | VG Somasekhar Managing Director Airtel Uganda |
Henceforth, Attackers successfully launched attacks on Thursday night, went successful through Friday, only for their presence to be noticed on Saturday 3rd October.
In a bid to block the attackers activity, MTN and Airtel blocked access to mobile money accounts as a measure to implement a Denial of Service (DOS) status to safeguard customer accounts.
However, this did go well with unsuspecting customers who took waged war on the hosting telcos via Twitter and shared their grievances.
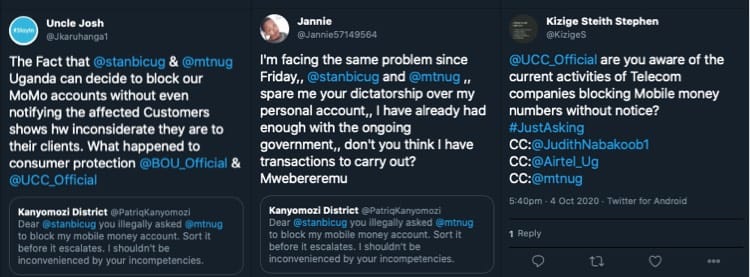
At the moment, Stanbic Bank has also activated a DOS (Denial of Service) mode blocking their *290# mobile banking service until the root cause of the attack is identified, and the backdoor sealed to avoid future incidences.
For now, security authorities are on the hunt for the group of black hat hackers who may have robbed MTN, Airtel, and Stanbic in a period of less than 3-days with rogue transactions performed through a 3rd party provider system.
